Objectifs de certification
ENCOR 350-401
3.2 Layer 3 : 3.2.c Configure and verify eBGP between directly connected neighbors (best path selection algorithm and neighbor relationships)
Lab Cisco WAN
En cours de rédaction
Dans cet exercice de lab, on illustrera la configuration et le diagnostic de connexions PPP, MLPPP et PPPoE avec l’authentification, le protocole de tunnel GRE et le protcole de routage EBGP.
1. Configuration de base avec NAT
- R2 :
vios-adventerprisek9-m.vmdk.SPA.156-2.T - R1 et R3 :
c3725-adventerprisek9-mz.124-15.T14.image+ 1 WIC-2T + 256 MB RAM
R2 et R3 sont des routeurs qui se connectent à un Fournisseur d’Accès Internet via des lignes Ethernet et Série.
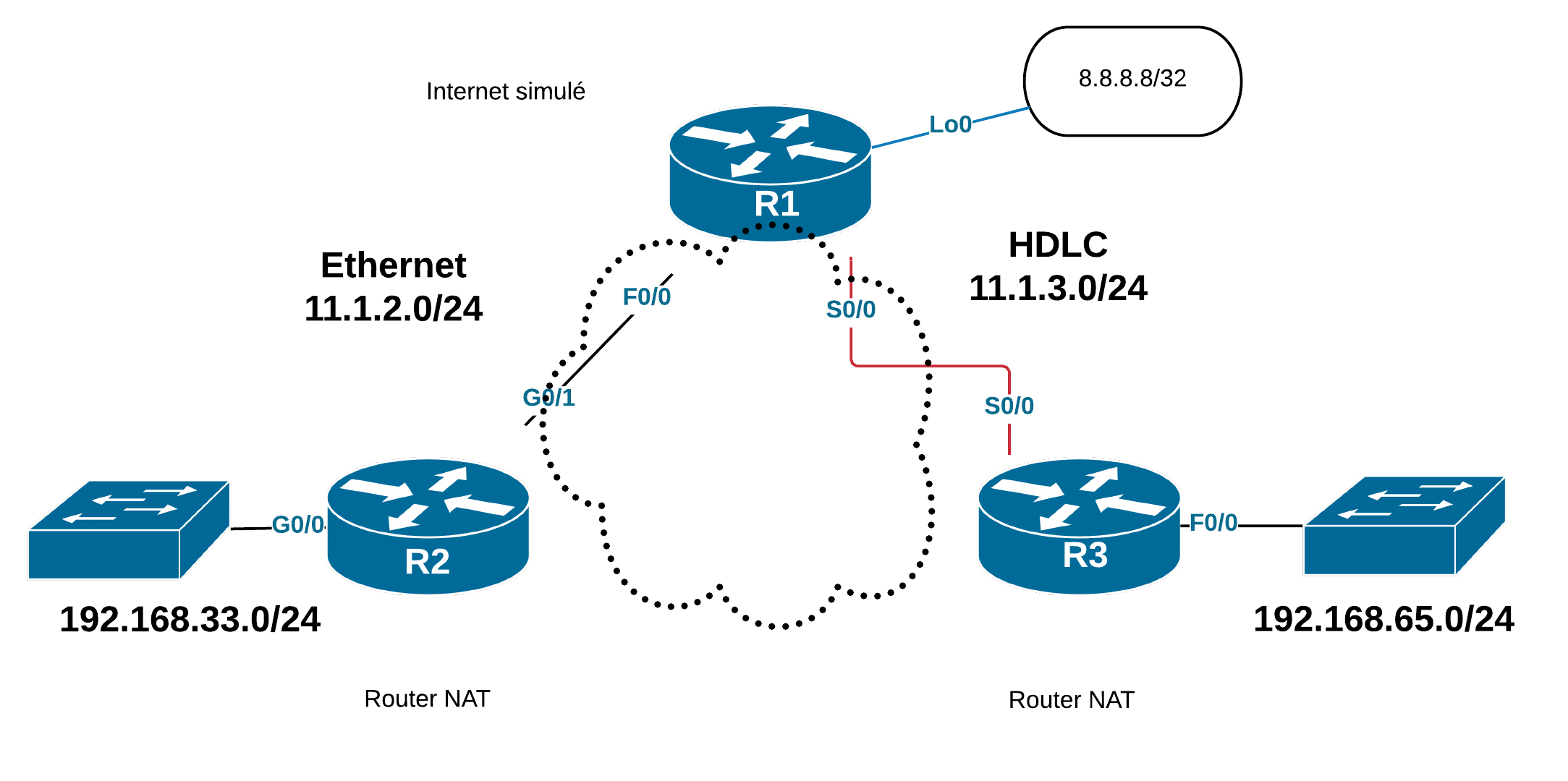
Deux sites se connectent à l’Internet représenté par les blocs publics 11.1.2.0/24 et 11.1.3.0/24 (bloc du DoD américain). Chacun des sites hébergent un réseau privé adressé en 192.168.33.0/24 sur R2 et en 192.168.65.0/24 sur R3. R1 simule un routeur dans l’Internet public.
Dans ce scénario de départ, on configure les interfaces Ethernet et Série (encapsulation HDLC par défaut). Le NAT est activé sur les deux routeurs d’extrémité.
hostname R1
!
int f0/0
ip add 11.1.2.1 255.255.255.0
no shutdown
int s0/0
ip add 11.1.3.1 255.255.255.0
no shutdown
int lo0
ip add 8.8.8.8 255.255.255.255
!
end
!
wr
hostname R2
!
ip dhcp pool LAN
network 192.168.33.0 255.255.255.0
default-router 192.168.33.1
!
no ip domain lookup
ip cef
!
interface G0/0
ip address 192.168.33.1 255.255.255.0
ip nat inside
no shutdown
!
interface G0/1
ip address 11.1.2.2 255.255.255.0
ip nat outside
no shutdown
!
ip nat inside source list LAN interface G0/1 overload
ip route 0.0.0.0 0.0.0.0 11.1.2.1 254
!
ip access-list extended LAN
permit ip 192.168.33.0 0.0.0.255 any
!
end
!
wr
hostname R3
!
ip dhcp pool LAN
network 192.168.66.0 255.255.255.0
default-router 192.168.66.1
!
no ip domain lookup
ip cef
!
interface F0/0
ip address 192.168.66.1 255.255.255.0
ip nat inside
no shutdown
!
interface S0/0
ip address 11.1.3.2 255.255.255.0
ip nat outside
no shutdown
!
ip nat inside source list LAN interface S0/0 overload
ip route 0.0.0.0 0.0.0.0 11.1.3.1 254
!
ip access-list extended LAN
permit ip 192.168.66.0 0.0.0.255 any
!
end
!
wr
1.1. Table de routage (R2)
R2#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is 11.1.2.1 to network 0.0.0.0
S* 0.0.0.0/0 [254/0] via 11.1.2.1
11.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 11.1.2.0/24 is directly connected, GigabitEthernet0/1
L 11.1.2.2/32 is directly connected, GigabitEthernet0/1
192.168.33.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.33.0/24 is directly connected, GigabitEthernet0/0
L 192.168.33.1/32 is directly connected, GigabitEthernet0/0
1.2. Connectivité de bout en bout (R2)
R2#ping 11.1.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 11.1.2.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/9/10 ms
R2#ping 8.8.8.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 6/9/10 ms
R2#ping 11.1.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 11.1.3.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 9/10/14 ms
R2#ping 11.1.3.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 11.1.3.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 9/13/28 ms
R2#ping
Protocol [ip]:
Target IP address: 11.1.3.2
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Ingress ping [n]:
Source address or interface: 192.168.33.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0x0000ABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 11.1.3.2, timeout is 2 seconds:
Packet sent with a source address of 192.168.33.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/11/15 ms
R2#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 11.1.2.2:6 192.168.33.1:6 11.1.3.2:6 11.1.3.2:6
R2#
1.3. Conectivité locale (R3 S0/0)
Vérification du statut de l’interface et de l’encapsulation :
R3#show interfaces s0/0
Serial0/0 is up, line protocol is up
Hardware is GT96K Serial
Internet address is 11.1.3.2/24
MTU 1500 bytes, BW 1544 Kbit/sec, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation HDLC, loopback not set
Keepalive set (10 sec)
CRC checking enabled
...
Serial0/0 is up, line protocol is up et Encapsulation HDLC.
Couche physique :
R3#show controllers s0/0
Interface Serial0/0
Hardware is GT96K
DCE 530, clock rate 2000000
idb at 0x665D7118, driver data structure at 0x665DE824
...
DCE 530, clock rate 2000000
Etat de l’interface :
R3#show ip interface brief | include Serial0/0
Serial0/0 11.1.3.2 YES manual up up
Si CDP répond, la couche 2 est opérationnelle sur la liaison :
R3#show cdp neighbors
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater
Device ID Local Intrfce Holdtme Capability Platform Port ID
R1 Ser 0/0 133 R S I 3725 Ser 0/0
R3#
1.4. Capture de trafic HDLC
Capture de trafic CDP et ICMP entre R1 et R3 sur les lignes séries supportées en HDLC Cisco : https://www.cloudshark.org/captures/6255ac5699a2
Frame 3: 104 bytes on wire (832 bits), 104 bytes captured (832 bits)
Cisco HDLC
Address: Unicast (0x0f)
Control: 0x00
Protocol: IP (0x0800)
Internet Protocol Version 4, Src: 11.1.2.2, Dst: 11.1.3.2
Internet Control Message Protocol
2. PPP et PPP CHAP
2.1. Activation de PPP
Activation de l’encapsulation PPP sur l’interface S0/0 de R1 et R3.
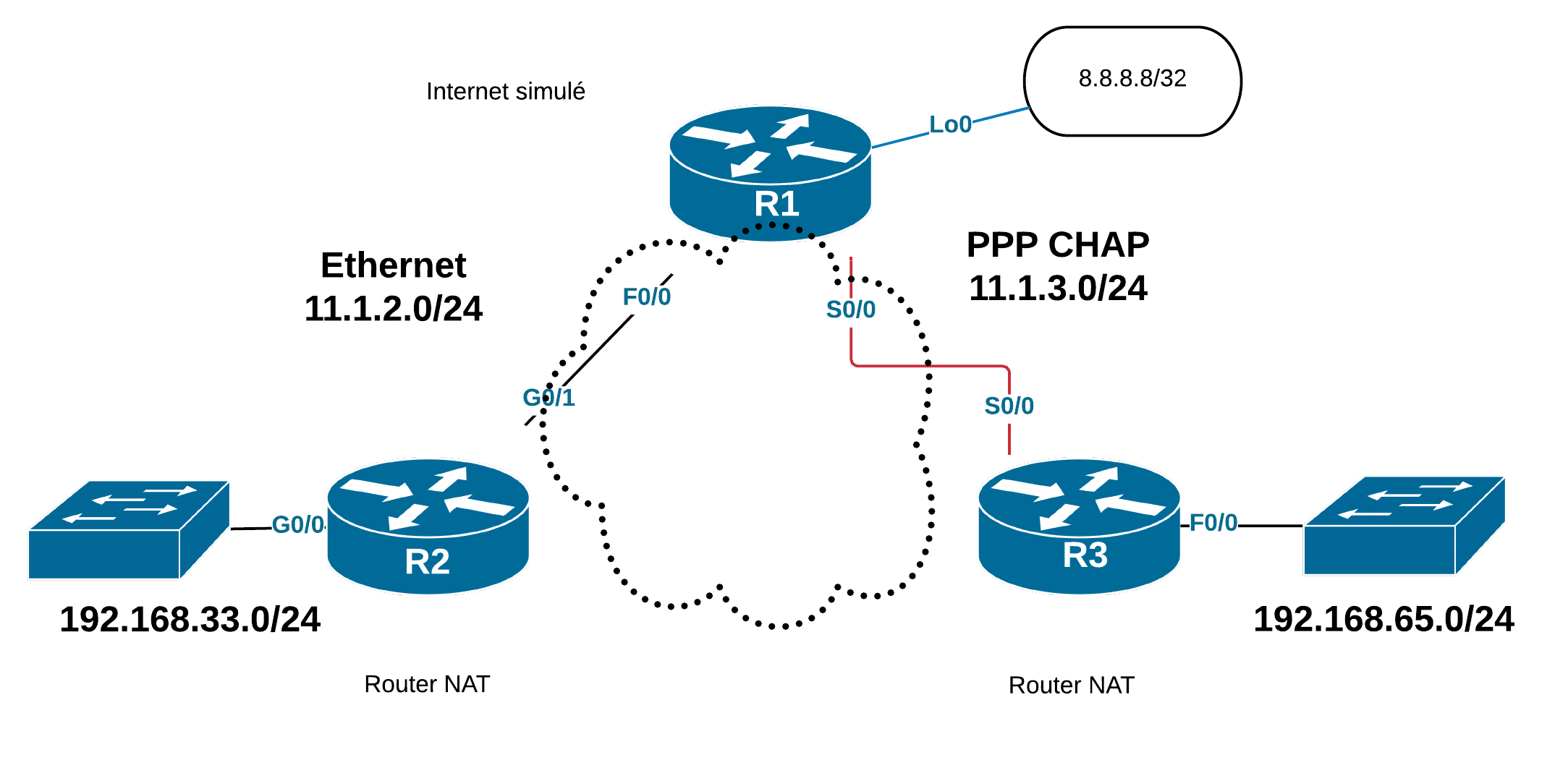
En configuration de l’interface s0/0, on change l’encapsulation par défaut hdlc en encapsulation ppp. On constate qu’il y a d’autres protocoles disponibles.
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#int s0/0
R1(config-if)#encapsulation ?
bstun Block Serial tunneling (BSTUN)
frame-relay Frame Relay networks
hdlc Serial HDLC synchronous
lapb LAPB (X.25 Level 2)
ppp Point-to-Point protocol
sdlc SDLC
sdlc-primary SDLC (primary)
sdlc-secondary SDLC (secondary)
smds Switched Megabit Data Service (SMDS)
stun Serial tunneling (STUN)
x25 X.25
R1(config-if)#encapsulation ppp
R1(config-if)#^Z
R1#
*Mar 1 00:06:14.883: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to down
*Mar 1 00:06:15.299: %SYS-5-CONFIG_I: Configured from console by console
Les derniers “logs” nous indiquent que l’interface ne s’est pas montée. Le diagnostic de l’interface est up/down qui présume un problème L2, ici une encapsulation L2 différente sur la même liaison : PPP du côté de R1 et HDLC toujours pour l’instant sur R3.
R1#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 11.1.2.1 YES manual up up
Serial0/0 11.1.3.1 YES manual up down
FastEthernet0/1 unassigned YES unset administratively down down
Serial0/1 unassigned YES unset administratively down down
Loopback0 8.8.8.8 YES manual up up
R1#
En plaçant la bonne configuration sur R3, l’interface se monte :
R3(config)#int s0/0
R3(config-if)#encapsulation ppp
*Mar 1 00:06:55.991: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to up
R1#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 11.1.2.1 YES manual up up
Serial0/0 11.1.3.1 YES manual up up
FastEthernet0/1 unassigned YES unset administratively down down
Serial0/1 unassigned YES unset administratively down down
Loopback0 8.8.8.8 YES manual up up
R1#
*Mar 1 00:07:17.531: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to down
*Mar 1 00:07:19.551: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to up
*Mar 1 00:10:34.279: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to down
*Mar 1 00:10:36.303: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to up
2.2. Activation de PPP CHAP
Activation de PPP CHAP entre R1 et R3.
R1(config)#username R3 password testtest
R1(config)#int s0/0
R1(config-if)#encapsulation ppp
R1(config-if)#ppp authentication chap
Tant que l’interface correspondante n’est pas configurée avec le bon mot de passe, on connait encore un diagnostic up/down.
R3(config)#username R1 password testtest
R3(config)#int s0/0
R3(config-if)#encapsulation ppp
R3(config-if)#ppp authentication chap
2.3. Encapsulation PPP
R3#show interfaces s0/0
Serial0/0 is up, line protocol is up
Hardware is GT96K Serial
Internet address is 11.1.3.2/24
MTU 1500 bytes, BW 1544 Kbit/sec, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, LCP Open
Open: IPCP, CDPCP, loopback not set
Keepalive set (10 sec)
CRC checking enabled
Les lignes de la sortie “Encapsulation PPP, LCP Open” et “Open: IPCP, CDPCP, loopback not set” indiquent que les deux phases LCP et NCP se sont déroulées avec succès.
2.4. Débogage ppp negotiation
R3#debug ppp negotiation
PPP protocol negotiation debugging is on
R3#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#interface s0/0
R3(config-if)#shutdown
*Mar 1 00:14:02.471: %LINK-5-CHANGED: Interface Serial0/0, changed state to administratively down
R3(config-if)#
*Mar 1 00:14:02.475: Se0/0 PPP: Sending Acct Event[Down] id[3]
*Mar 1 00:14:02.479: Se0/0 CDPCP: State is Closed
*Mar 1 00:14:02.479: Se0/0 IPCP: State is Closed
*Mar 1 00:14:02.483: Se0/0 PPP: Phase is TERMINATING
*Mar 1 00:14:02.483: Se0/0 LCP: State is Closed
*Mar 1 00:14:02.483: Se0/0 PPP: Phase is DOWN
*Mar 1 00:14:02.487: Se0/0 IPCP: Remove route to 11.1.3.1
*Mar 1 00:14:03.471: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to down
R3(config-if)#no shutdown
*Mar 1 00:14:16.271: Se0/0 PPP: Outbound cdp packet dropped
*Mar 1 00:14:18.263: %LINK-3-UPDOWN: Interface Serial0/0, changed state to up
*Mar 1 00:14:18.267: Se0/0 PPP: Using default call direction
*Mar 1 00:14:18.271: Se0/0 PPP: Treating connection as a dedicated line
*Mar 1 00:14:18.271: Se0/0 PPP: Session handle[4C000003] Session id[4]
*Mar 1 00:14:18.271: Se0/0 PPP: Phase is ESTABLISHING, Active Open
*Mar 1 00:14:18.271: Se0/0 LCP: O CONFREQ [Closed] id 4 len 15
*Mar 1 00:14:18.275: Se0/0 LCP: AuthProto CHAP (0x0305C22305)
*Mar 1 00:14:18.275: Se0/0 LCP: MagicNumber 0x0155D6D8 (0x05060155D6D8)
*Mar 1 00:14:18.287: Se0/0 LCP: I CONFREQ [REQsent] id 6 len 15
*Mar 1 00:14:18.287: Se0/0 LCP: AuthProto CHAP (0x0305C22305)
*Mar 1 00:14:18.287: Se0/0 LCP: MagicNumber 0x0255E5CA (0x05060255E5CA)
*Mar 1 00:14:18.291: Se0/0 LCP: O CONFACK [REQsent] id 6 len 15
*Mar 1 00:14:18.291: Se0/0 LCP: AuthProto CHAP (0x0305C22305)
*Mar 1 00:14:18.291: Se0/0 LCP: MagicNumber 0x0255E5CA (0x05060255E5CA)
*Mar 1 00:14:18.295: Se0/0 LCP: I CONFACK [ACKsent] id 4 len 15
*Mar 1 00:14:18.295: Se0/0 LCP: AuthProto CHAP (0x0305C22305)
*Mar 1 00:14:18.295: Se0/0 LCP: MagicNumber 0x0155D6D8 (0x05060155D6D8)
*Mar 1 00:14:18.295: Se0/0 LCP: State is Open
*Mar 1 00:14:18.299: Se0/0 PPP: Phase is AUTHENTICATING, by both
*Mar 1 00:14:18.299: Se0/0 CHAP: O CHALLENGE id 2 len 23 from "R3"
*Mar 1 00:14:18.315: Se0/0 CHAP: I CHALLENGE id 3 len 23 from "R1"
*Mar 1 00:14:18.327: Se0/0 CHAP: Using hostname from unknown source
*Mar 1 00:14:18.327: Se0/0 CHAP: Using password from AAA
*Mar 1 00:14:18.327: Se0/0 CHAP: O RESPONSE id 3 len 23 from "R3"
*Mar 1 00:14:18.327: Se0/0 CHAP: I RESPONSE id 2 len 23 from "R1"
*Mar 1 00:14:18.327: Se0/0 PPP: Phase is FORWARDING, Attempting Forward
*Mar 1 00:14:18.327: Se0/0 PPP: Phase is AUTHENTICATING, Unauthenticated User
*Mar 1 00:14:18.331: Se0/0 PPP: Phase is FORWARDING, Attempting Forward
*Mar 1 00:14:18.331: Se0/0 PPP: Phase is AUTHENTICATING, Authenticated User
*Mar 1 00:14:18.339: Se0/0 CHAP: I SUCCESS id 3 len 4
*Mar 1 00:14:18.339: Se0/0 CHAP: O SUCCESS id 2 len 4
*Mar 1 00:14:18.343: Se0/0 PPP: Phase is UP
*Mar 1 00:14:18.343: Se0/0 IPCP: O CONFREQ [Closed] id 1 len 10
*Mar 1 00:14:18.343: Se0/0 IPCP: Address 11.1.3.2 (0x03060B010302)
*Mar 1 00:14:18.343: Se0/0 PPP: Process pending ncp packets
*Mar 1 00:14:18.347: Se0/0 IPCP: I CONFREQ [REQsent] id 1 len 10
*Mar 1 00:14:18.347: Se0/0 IPCP: Address 11.1.3.1 (0x03060B010301)
*Mar 1 00:14:18.347: Se0/0 AAA/AUTHOR/IPCP: Start. Her address 11.1.3.1, we want 0.0.0.0
*Mar 1 00:14:18.351: Se0/0 CDPCP: I CONFREQ [Closed] id 1 len 4
*Mar 1 00:14:18.351: Se0/0 AAA/AUTHOR/IPCP: Reject 11.1.3.1, using 0.0.0.0
*Mar 1 00:14:18.351: Se0/0 AAA/AUTHOR/IPCP: Done. Her address 11.1.3.1, we want 0.0.0.0
*Mar 1 00:14:18.351: Se0/0 IPCP: O CONFACK [REQsent] id 1 len 10
*Mar 1 00:14:18.351: Se0/0 IPCP: Address 11.1.3.1 (0x03060B010301)
*Mar 1 00:14:18.351: Se0/0 IPCP: I CONFACK [ACKsent] id 1 len 10
*Mar 1 00:14:18.351: Se0/0 IPCP: Address 11.1.3.2 (0x03060B010302)
*Mar 1 00:14:18.351: Se0/0 IPCP: State is Open
*Mar 1 00:14:18.355: Se0/0 CDPCP: O CONFREQ [Closed] id 1 len 4
*Mar 1 00:14:18.363: Se0/0 IPCP: Install route to 11.1.3.1
*Mar 1 00:14:18.363: Se0/0 CDPCP: I CONFACK [REQsent] id 1 len 4
*Mar 1 00:14:19.343: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to up
*Mar 1 00:14:20.355: Se0/0 CDPCP: Timeout: State ACKrcvd
*Mar 1 00:14:20.355: Se0/0 CDPCP: O CONFREQ [ACKrcvd] id 2 len 4
*Mar 1 00:14:20.371: Se0/0 CDPCP: I CONFACK [REQsent] id 2 len 4
*Mar 1 00:14:20.375: Se0/0 CDPCP: I CONFREQ [ACKrcvd] id 2 len 4
*Mar 1 00:14:20.375: Se0/0 CDPCP: O CONFACK [ACKrcvd] id 2 len 4
*Mar 1 00:14:20.375: Se0/0 CDPCP: State is Open
R3(config-if)#^Z
R3#undebug all
All possible debugging has been turned off
R3#
2.5. Débogage ppp authentication
R3#debug ppp authentication
PPP authentication debugging is on
R3#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#interface s0/0
R3(config-if)#shutdown
*Mar 1 00:17:36.671: %LINK-5-CHANGED: Interface Serial0/0, changed state to administratively down
*Mar 1 00:17:37.671: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to down
R3(config-if)#no shutdown
*Mar 1 00:17:56.467: %LINK-3-UPDOWN: Interface Serial0/0, changed state to up
*Mar 1 00:17:56.471: Se0/0 PPP: Using default call direction
*Mar 1 00:17:56.475: Se0/0 PPP: Treating connection as a dedicated line
*Mar 1 00:17:56.475: Se0/0 PPP: Session handle[F6000004] Session id[5]
*Mar 1 00:17:56.475: Se0/0 PPP: Authorization required
*Mar 1 00:17:56.507: Se0/0 CHAP: O CHALLENGE id 3 len 23 from "R3"
*Mar 1 00:17:56.527: Se0/0 CHAP: I CHALLENGE id 4 len 23 from "R1"
*Mar 1 00:17:56.535: Se0/0 CHAP: Using hostname from unknown source
*Mar 1 00:17:56.535: Se0/0 CHAP: Using password from AAA
*Mar 1 00:17:56.535: Se0/0 CHAP: O RESPONSE id 4 len 23 from "R3"
*Mar 1 00:17:56.535: Se0/0 CHAP: I RESPONSE id 3 len 23 from "R1"
*Mar 1 00:17:56.543: Se0/0 PPP: Sent CHAP LOGIN Request
*Mar 1 00:17:56.543: Se0/0 PPP: Received LOGIN Response PASS
*Mar 1 00:17:56.547: Se0/0 PPP: Sent LCP AUTHOR Request
*Mar 1 00:17:56.547: Se0/0 PPP: Sent IPCP AUTHOR Request
*Mar 1 00:17:56.551: Se0/0 CHAP: I SUCCESS id 4 len 4
*Mar 1 00:17:56.551: Se0/0 LCP: Received AAA AUTHOR Response PASS
*Mar 1 00:17:56.555: Se0/0 IPCP: Received AAA AUTHOR Response PASS
*Mar 1 00:17:56.555: Se0/0 CHAP: O SUCCESS id 3 len 4
*Mar 1 00:17:56.559: Se0/0 PPP: Sent CDPCP AUTHOR Request
*Mar 1 00:17:56.559: Se0/0 PPP: Sent IPCP AUTHOR Request
*Mar 1 00:17:56.563: Se0/0 CDPCP: Received AAA AUTHOR Response PASS
*Mar 1 00:17:57.555: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to up
R3(config-if)#^Z
R3#undebug all
All possible debugging has been turned off
R3#
2.6. Capture de trafic PPP CHAP
https://www.cloudshark.org/captures/d31c4bd21ebc
3. MLPPP
MLPPP (PPP Multilink) est la variante du protocole PPP qui permet d’agréger des liaisons physiques pour créer un seul canal logique. Le protocole permet de répartir la charge sur les liaisons cumulées et offre un certain niveau de redondance en cas de rupture d’une des liaisons physiques.
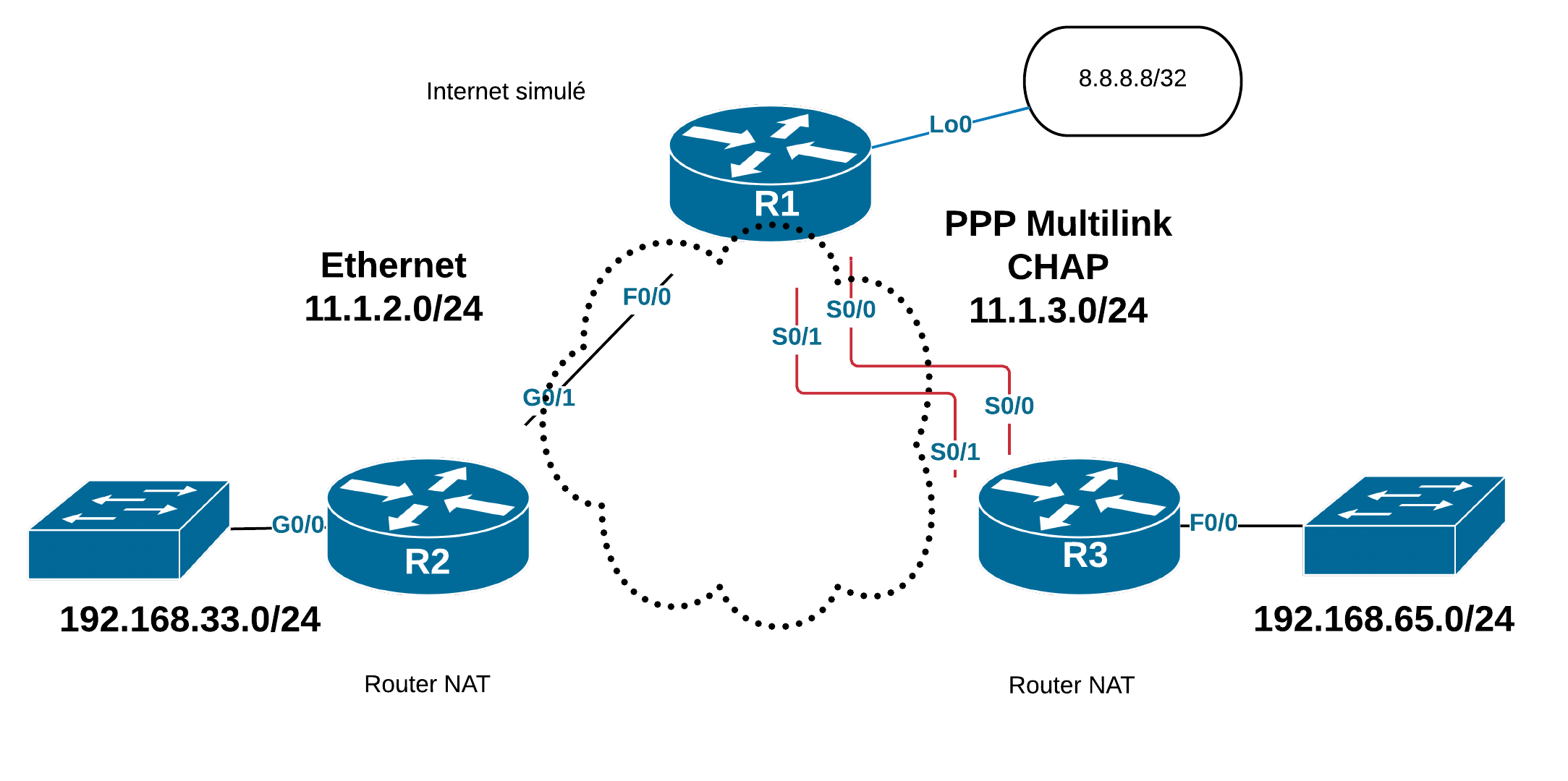
Dans ce scénario, on ajoute une interface S0/0 et une interface S0/1 au groupe ppp multilink 1.
3.1. Configuration MLPPP
Sur R1 :
R1(config)#int s0/0
R1(config-if)#no ip address
R1(config-if)#encapsulation ppp
R1(config-if)#ppp multilink
R1(config-if)#ppp multilink group 1
R1(config-if)#int s0/1
R1(config-if)#encapsulation ppp
R1(config-if)#ppp authentication chap
R1(config-if)#ppp multilink
R1(config-if)#ppp multilink group 1
R1(config-if)#no shutdown
R1(config-if)#int multi 1
R1(config-if)#encapsulation ppp
R1(config-if)#ppp multilink
R1(config-if)#ppp multilink group 1
R1(config-if)#ip add 11.1.3.1 255.255.255.0
R1(config-if)#exit
Sur R3 :
R3(config)#int s0/0
R3(config-if)#no ip address
R3(config-if)#encapsulation ppp
R3(config-if)#ppp multilink
R3(config-if)#ppp multilink group 1
R3(config-if)#ip nat outside
R3(config-if)#int s0/1
R3(config-if)#encapsulation ppp
R3(config-if)#ppp authentication chap
R3(config-if)#ppp multilink
R3(config-if)#ppp multilink group 1
R3(config-if)#no shutdown
R3(config-if)#int multi 1
R3(config-if)#encapsulation ppp
R3(config-if)#ppp multilink
R3(config-if)#ppp multilink group 1
R3(config-if)#ip add 11.1.3.2 255.255.255.0
R3(config-if)#ip nat outside
R3(config-if)#exit
On prendra garde d’adapter la configuration NAT sur R3 puisque le nom de l’interface externe change.
R3(config)#no ip nat inside source list LAN interface Serial0/0 overload
R3(config)#ip nat inside source list LAN interface multi 1 overload
3.2. Diagnostic MLPPP
R3#show ppp multilink interface multilink 1
Multilink1
Bundle name: R1
Remote Username: R1
Remote Endpoint Discriminator: [1] R1
Local Username: R3
Local Endpoint Discriminator: [1] R3
Bundle up for 02:37:42, total bandwidth 3088, load 1/255
Receive buffer limit 24000 bytes, frag timeout 1000 ms
0/0 fragments/bytes in reassembly list
0 lost fragments, 0 reordered
0/0 discarded fragments/bytes, 0 lost received
0x13B received sequence, 0x13D sent sequence
Member links: 2 active, 0 inactive (max not set, min not set)
Se0/0, since 02:37:43
Se0/1, since 02:37:40
R3#show interfaces multilink 1
Multilink1 is up, line protocol is up
Hardware is multilink group interface
Internet address is 11.1.3.2/24
MTU 1500 bytes, BW 3088 Kbit/sec, DLY 100000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, LCP Open, multilink Open
Open: IPCP, CDPCP, loopback not set
Keepalive set (10 sec)
DTR is pulsed for 2 seconds on reset
Last input 00:00:20, output never, output hang never
Last clearing of "show interface" counters 02:38:04
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
164 packets input, 53152 bytes, 0 no buffer
Received 0 Broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
165 packets output, 54936 bytes, 0 underruns
0 output errors, 0 collisions, 1 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped out
Où BW 3088 Kbit/sec
4. PPPoE
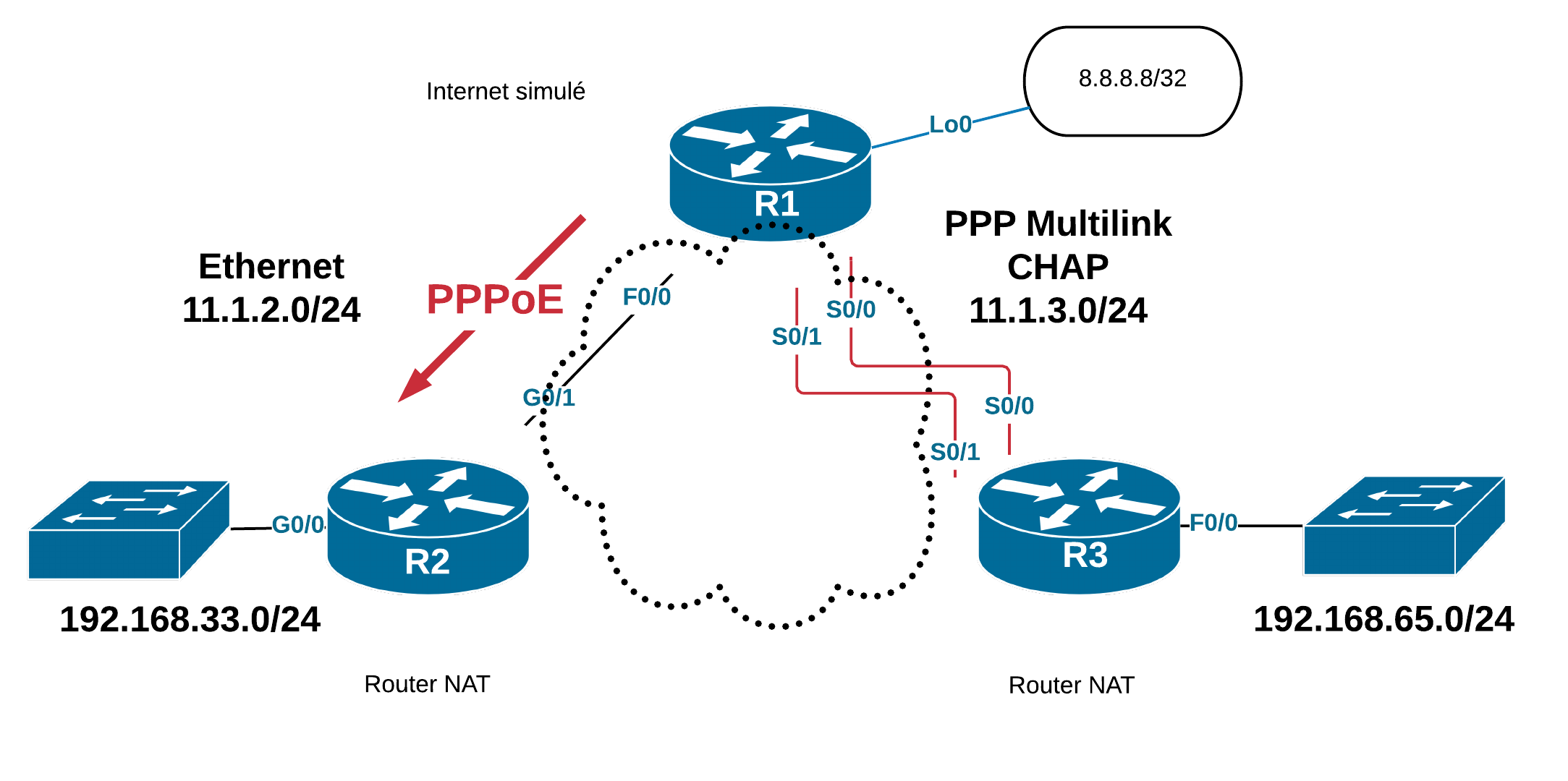
- R1 est serveur PPPoE.
- R2 est client PPPoE
- Username : client1
- Password : testtest
4.1. Configurations
Configuration Client R2 :
Il est nécessaire d’adapter la configuration NAT
interface G0/1
no ip address
no shutdown
no ip redirects
no ip unreachables
no ip proxy-arp
ip tcp adjust-mss 1452
pppoe enable
pppoe-client dial-pool-number 1
no ip nat outside
!
interface Dialer1
ip address negotiated
encapsulation ppp
dialer pool 1
dialer-group 1
no cdp enable
ppp authentication pap chap callin
ppp pap sent-username client1 password testtest
ppp chap hostname client1
ppp chap password testtest
ip nat outside
!
no ip nat inside source list LAN interface GigabitEthernet0/1 overload
ip nat inside source list LAN interface Dialer1 overload
Configuration Serveur :
username client1 secret testtest
!
bba-group pppoe global
virtual-template 1
!
interface F0/0
load-interval 30
pppoe enable group global
ip add 11.1.2.1 255.255.255.0
no shutdown
!
interface Virtual-Template1
mtu 1492
ip unnumbered F0/0
peer default ip address pool pppoepool
ppp authentication pap chap
!
ip local pool pppoepool 11.1.2.100 11.1.2.109
4.2. Diagnostic
R2#show interfaces dialer 1
Dialer1 is up, line protocol is up (spoofing)
Hardware is Unknown
Internet address is 10.1.2.100/32
MTU 1500 bytes, BW 56 Kbit/sec, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, LCP Closed, loopback not set
Keepalive set (10 sec)
DTR is pulsed for 1 seconds on reset
Interface is bound to Vi2
...
R2#show ip interface dialer 1
Dialer1 is up, line protocol is up
Internet address is 10.1.2.100/32
Broadcast address is 255.255.255.255
Address determined by IPCP
MTU is 1500 bytes
...
5. Tunnel GRE
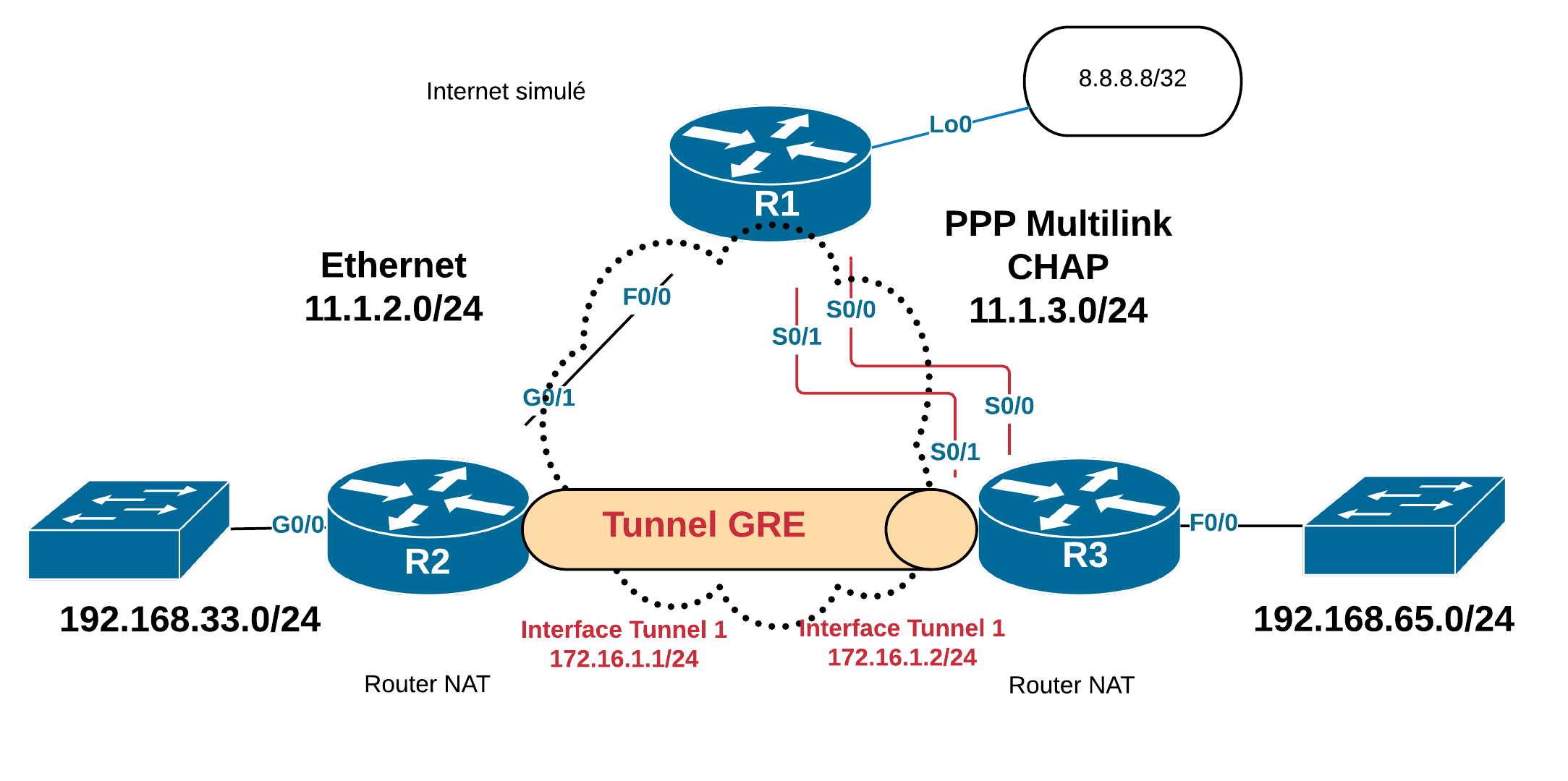
Dans ce scénario, on propose de créer un tunnel GRE entre R2 et R3 pour connecter leur LAN. Les adresses du tunnel sont des adresses privées. 172.16.1.1/24 (R2) et 172.16.1.2/24 (R3) sont choisis.
5.1. Configuration
Sur R2 :
interface Tunnel1
ip address 172.16.1.1 255.255.255.0
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source dialer 1
tunnel destination 11.1.3.2
ip route 192.168.66.0 255.255.255.0 172.16.1.2
Sur R3 :
interface Tunnel1
ip address 172.16.1.2 255.255.255.0
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source 11.1.3.2
tunnel destination 11.1.2.100
ip route 192.168.33.0 255.255.255.0 172.16.1.1
5.2. Diagnostic GRE
Ping étendu du LAN de R2 au LAN de R3 :
R2#ping
Protocol [ip]:
Target IP address: 192.168.66.1
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Ingress ping [n]:
Source address or interface: 192.168.33.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0x0000ABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.66.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.33.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/13/26 ms
5.3. Capture de trafic
Capture du trafic : https://www.cloudshark.org/captures/07b9bbcbfdc3
Frame 8: 146 bytes on wire (1168 bits), 146 bytes captured (1168 bits) on interface 0
Ethernet II, Src: 00:66:a6:59:2a:01 (00:66:a6:59:2a:01), Dst: c2:02:48:cd:00:00 (c2:02:48:cd:00:00)
PPP-over-Ethernet Session
Point-to-Point Protocol
Internet Protocol Version 4, Src: 11.1.2.100, Dst: 11.1.3.2
Generic Routing Encapsulation (IP)
Internet Protocol Version 4, Src: 192.168.33.1, Dst: 192.168.66.1
Internet Control Message Protocol
6. eBGP
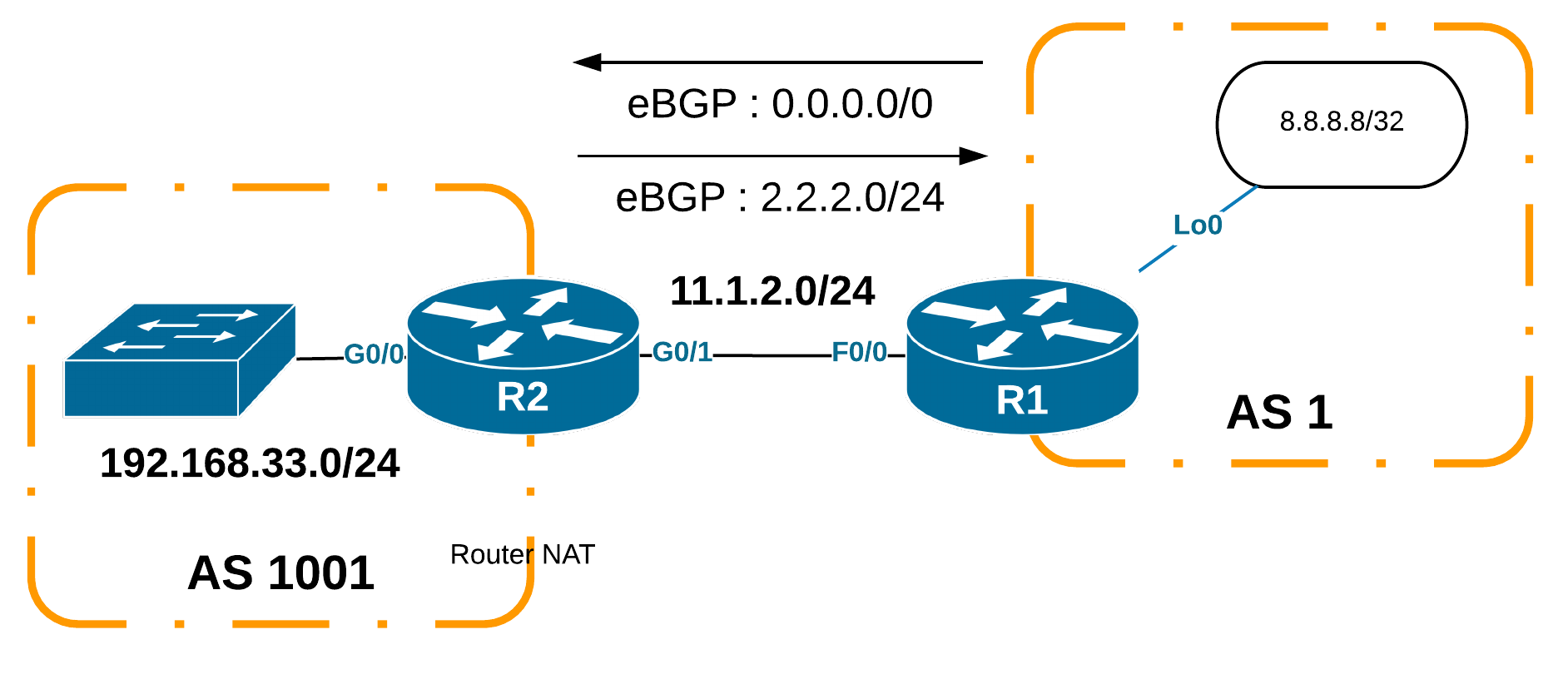
Dans ce scénario, R1 est le routeur ISP qui annonce une route par défaut. R2 annonce un réseau public 2.2.2.0/24.
6.1. Configuration eBGP ISP
hostname R1
!
interface Lo 0
ip address 8.8.8.8 255.0.0.0
!
interface F0/0
ip address 11.1.2.1 255.255.255.0
no shutdown
!
router bgp 1
network 0.0.0.0
neighbor 11.1.2.100 remote-as 1001
!
ip route 0.0.0.0 0.0.0.0 Null0
!
end
wr
6.2. Peering eBGP CPE
Etablir le peering :
R2(config)#router bgp 1001
R2(config-router)#neighbor 11.1.2.1 remote-as 1
Vérification :
R2#show tcp brief
TCB Local Address Foreign Address (state)
124E5488 11.1.2.100.45952 11.1.2.1.179 ESTAB
6.3. Annoncer un réseau CPE
Simulation d’un réseau :
R2(config)#interface lo1
R2(config-if)#ip address 2.2.2.1 255.255.255.0
Mais ce réseau pourrait être en DMZ et être appris via un protocole de routage dynamique.
Filtrage de l’annonce en eBGP :
R2(config)#router bgp 1001
R2(config-router)#network 2.2.2.0 mask 255.255.255.0
6.4. Vérification sur le routeur CPE
R2#show ip bgp
BGP table version is 3, local router ID is 192.168.33.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 0.0.0.0 11.1.2.1 0 0 1 i
*> 2.2.2.0/24 0.0.0.0 0 32768 i
R2#show ip route bgp | begin Gateway
Gateway of last resort is 11.1.2.1 to network 0.0.0.0
B* 0.0.0.0/0 [20/0] via 11.1.2.1, 00:02:00
6.5. Vérification routeur ISP
R1#show ip bgp
BGP table version is 3, local router ID is 8.8.8.8
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 0.0.0.0 0.0.0.0 0 32768 i
*> 2.2.2.0/24 11.1.2.100 0 0 1001 i

