Objectifs de certification
ENCOR 350-401
2.2 Configure and verify data path virtualization technologies
- 2.2.a VRF
- 2.2.b GRE and IPsec tunneling
Lab Configuration Cisco IOS IPSEC site-à-site, pre-shared, avec NAT overload entre réseaux privés
1. Présentation
Inspiré de : http://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-negotiation-ike-protocols/7276-overload-private.html
Voici un lab de configuration en Cisco IOS d’une topologie IPSEC VPN site-à-site, pre-shared, avec NAT overload entre deux réseaux privés. Il est démonstratif d’une configuration à l’aide de crypto-map.
2. Topologie
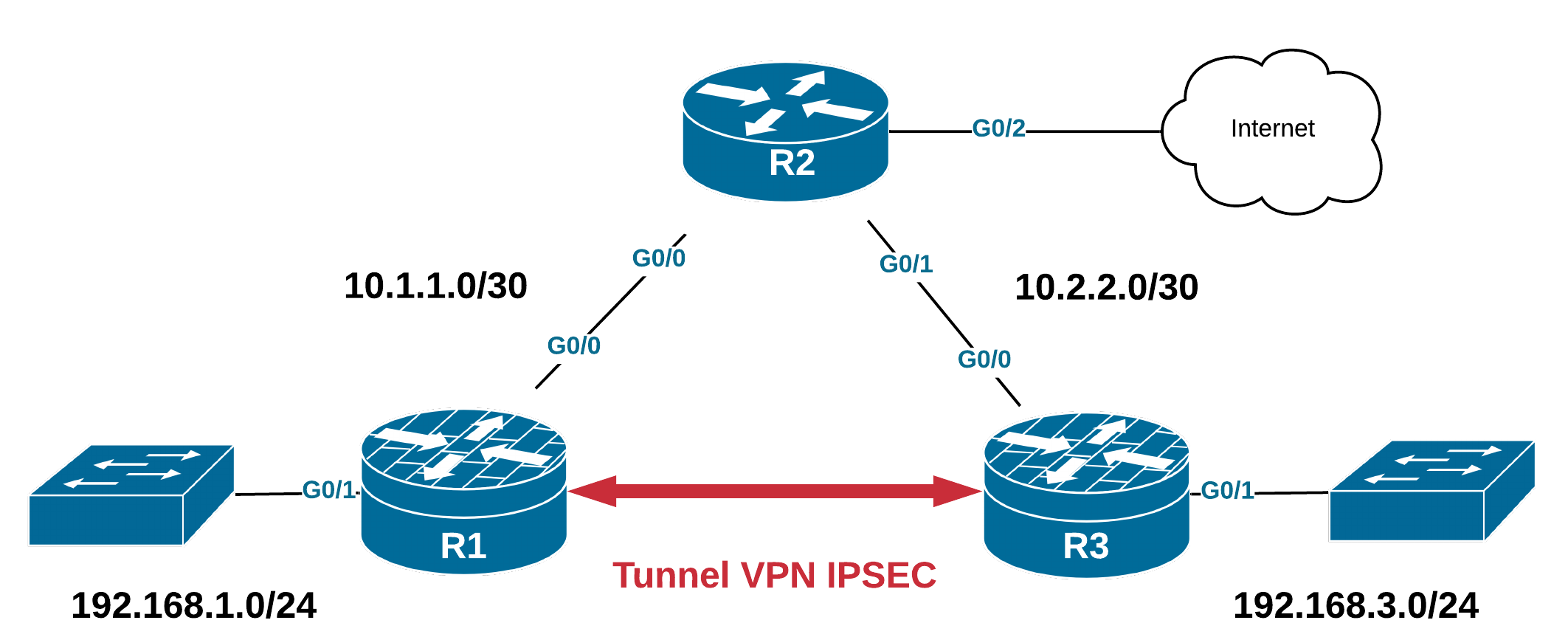
3. Evolution
- A intégrer avec un pare-feu ZBF.
- Remplacer un pare-feu IOS par un pare-feu ASA configuré en ASDM
- Remplacer un pare-feu IOS par un pare-feu ASA configuré en CLI
4. Procédure de Configuration
La procédure de configuration de configuration comporte six étapes :
- Créer un crypto-acl qui identifie le trafic du tunnel.
- Créer une ISAKMP policy pour la IKE SA.
- Configurer une clé partagée pour l’authentification ISAKMP.
- Créer un Transform Set qui indique le mode et les protocoles AH et ESP.
- Créer un Crypto-map qui indique la crypto-acl, l’adresse du pair et le Transform Set à utiliser.
- On applique le Crypto-map sur l’interafce externe.
Faudra-t-il en plus éviter de traduire le trafic d’un site à un autre.
5. Description
5.1. Règle NoNAT
…
5.2. IKE policy
- encryption algorithm: AES 256
- hash algorithm: sha1
- authentication method: Pre-Shared Key
- Diffie-Hellman group:
#5 - SA lifetime : 86400 seconds
Alors que les valeurs par défaut sont :
- encryption algorithm : DES (56 bits)
- hash algorithm : SHA1
- authentication method : RSA Signature
- Diffie-Hellman group :
#1 - SA lifetime : 86400 seconds
5.3. IPSEC
- un seul transform-set :
esp-256-aesetesp-sha-hmac
6. Configuration R1
hostname R1
!
crypto isakmp policy 1
encr aes 256
authentication pre-share
group 5
!
crypto isakmp key cisco123 address 10.2.2.1
!
crypto ipsec transform-set to-R3-set esp-aes 256 esp-sha-hmac
!
crypto map cm-to-R3 1 ipsec-isakmp
set peer 10.2.2.1
set transform-set to-R3-set
match address crypto-acl
!
interface G0/0
ip address 10.1.1.1 255.255.255.252
ip nat outside
no shutdown
crypto map cm-to-R3
!
interface G0/1
ip address 192.168.1.1 255.255.255.0 255.255.255.0
ip nat inside
no shutdown
!
ip route 0.0.0.0 0.0.0.0 10.1.1.2 222
!
ip nat inside source route-map nonat interface G0/0 overload
!
ip access-list extended nonat-acl
deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
permit ip 192.168.1.0 0.0.0.255 any
!
ip access-list extended crypto-acl
permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
!
route-map nonat permit 10
match ip address nonat-acl
!
end
7. Configuration R3
hostname R3
!
crypto isakmp policy 1
encr aes 256
authentication pre-share
group 5
!
crypto isakmp key cisco123 address 10.1.1.1
!
crypto ipsec transform-set to-R1-set esp-aes 256 esp-sha-hmac
!
crypto map cm-to-R1 1 ipsec-isakmp
set peer 10.1.1.1
set transform-set to-R1-set
match address crypto-acl
!
interface G0/0
ip address 10.2.2.1 255.255.255.252
ip nat outside
no shutdown
crypto map cm-to-R1
!
interface G0/1
ip address 192.168.3.1 255.255.255.0
ip nat inside
no shutdown
!
ip route 0.0.0.0 0.0.0.0 10.2.2.2 222
!
ip nat inside source route-map nonat interface G0/0 overload
!
ip access-list extended nonat-acl
deny ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255
permit ip 192.168.3.0 0.0.0.255 any
!
ip access-list extended crypto-acl
permit ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255
!
route-map nonat permit 10
match ip address nonat-acl
!
end
8. Diagnostic
8.1. Ping
R1#ping
Protocol [ip]:
Target IP address: 192.168.3.1
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Ingress ping [n]:
Source address or interface: 192.168.1.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0x0000ABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.3.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 4/4/4 ms
8.2. IKE Policy
R1#show crypto isakmp ?
key Show ISAKMP preshared keys
peers Show ISAKMP peer structures
policy Show ISAKMP protection suite policy
profile Show ISAKMP profiles
sa Show ISAKMP Security Associations
R1#show crypto isakmp policy
Global IKE policy
Protection suite of priority 1
encryption algorithm: AES - Advanced Encryption Standard (256 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #5 (1536 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
10.2.2.1 10.1.1.1 QM_IDLE 1001 ACTIVE
R1#show crypto isakmp peers
Peer: 10.2.2.1 Port: 500 Local: 10.1.1.1
Phase1 id: 10.2.2.1
8.3. IPSEC
Router_A#show crypto ipsec ?
client Show Client Status
policy Show IPSEC client policies
profile Show ipsec profile information
sa IPSEC SA table
security-association Show parameters for IPSec security associations
spi-lookup IPSEC SPI table
transform-set Crypto transform sets
R1#show crypto ipsec sa
interface: GigabitEthernet0/0
Crypto map tag: cm-to-R3, local addr 10.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0)
current_peer 10.2.2.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.1.1.1, remote crypto endpt.: 10.2.2.1
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0xBF70B56C(3211834732)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xD18F7FE4(3515842532)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80004040, crypto map: cm-to-R3
sa timing: remaining key lifetime (k/sec): (4204405/3496)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xBF70B56C(3211834732)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80004040, crypto map: cm-to-R3
sa timing: remaining key lifetime (k/sec): (4204405/3496)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R1#show crypto ipsec transform-set
Transform set default: { esp-aes esp-sha-hmac }
will negotiate = { Transport, },
Transform set to-R3-set: { esp-256-aes esp-sha-hmac }
will negotiate = { Tunnel, },
R1#show crypto ipsec transform-set
Transform set default: { esp-aes esp-sha-hmac }
will negotiate = { Transport, },
Transform set to-R3-set: { esp-256-aes esp-sha-hmac }
will negotiate = { Tunnel, },
R1#show crypto ipsec security-association
Security association lifetime: 4608000 kilobytes/3600 seconds
8.4. Debug IKE/IPSEC
R1#debug crypto isakmp
Crypto ISAKMP debugging is on
...
R1#debug crypto ipsec
Crypto IPSEC debugging is on
...

